
I explored asymmetric encryption algorithms and planned to implement them using Mathematica. But, I found the signing process somewhat complex, so I opted to use an existing tool for encryption and signing instead. OpenGPG is a suite of applications for encrypting and verifying messages. It uses the IDEA hashing algorithm for encryption and verification. It can encrypt and sign files, emails, and more. The corresponding software for Windows is GPG4WIN. Here is the information from Wikipedia: GNU Privacy Guard (GnuPG or GPG) is encryption software serving as a GPL-compliant alternative to PGP encryption software. Designed according to the OpenPGP technical standards set by the IETF, GnuPG facilitates encryption, digital signing, and asymmetric key pair generation. The IETF is standardizing the PGP protocol, known as OpenPGP. The current versions of PGP and Veridis’ Filecrypt are compatible with GnuPG and other OpenPGP systems. Funded by the German government currently, GnuPG is part of the GNU Project of the Free Software Foundation and is licensed under the GNU General Public License version 3.
Installation and Certificate Generation
GPG4WIN official website: https://www.gpg4win.org/
After downloading, proceed with the installation, including all additional components.
Upon installation, open Kleopatra to prepare for certificate generation. Kleopatra is a tool for managing certificates,
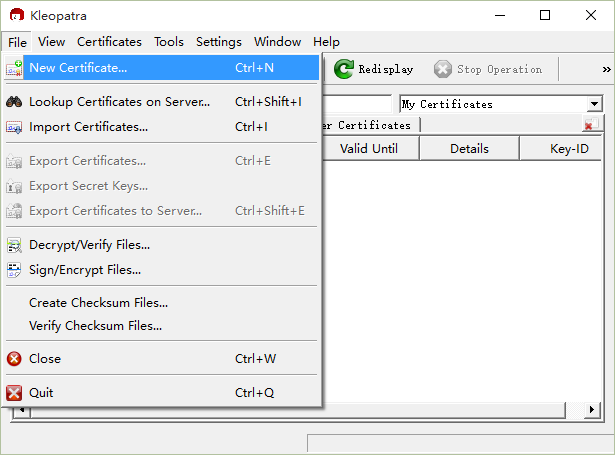
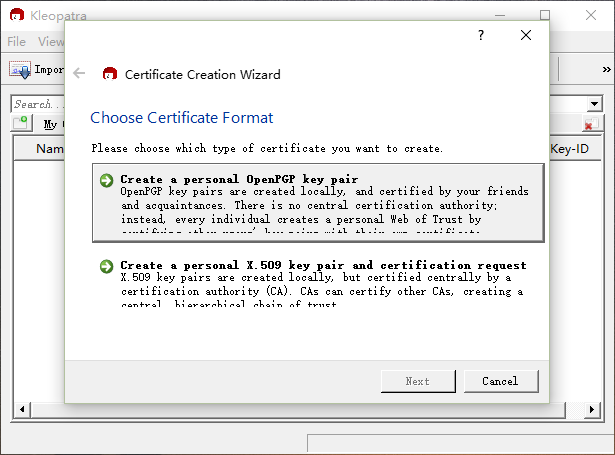
Select “personal OpenPGP key pair” to generate a personal key pair,
We need to fill out some information before generating the keys, as shown below,
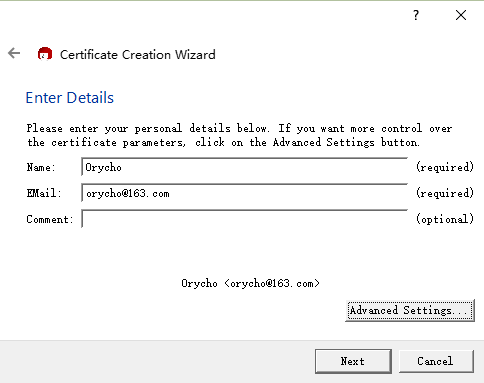
Click the “Advanced Setting…” button to access advanced settings, where we can select the encryption algorithms,
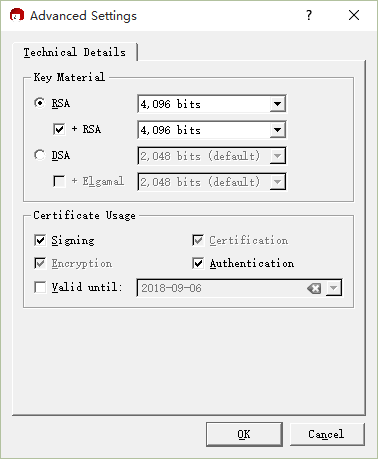
After completing this step, we’ll review the settings before finally setting a password,
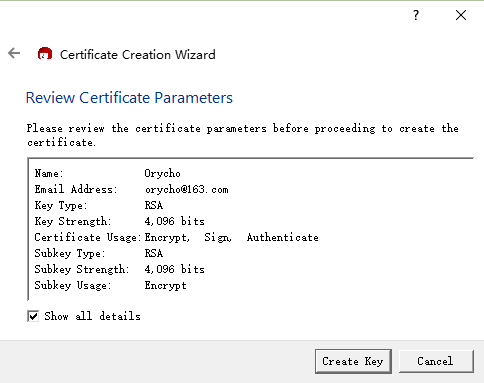
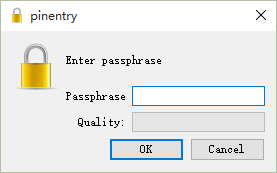
This password, combined with the private key, will allow the decryption of ciphertext encrypted with the public key,
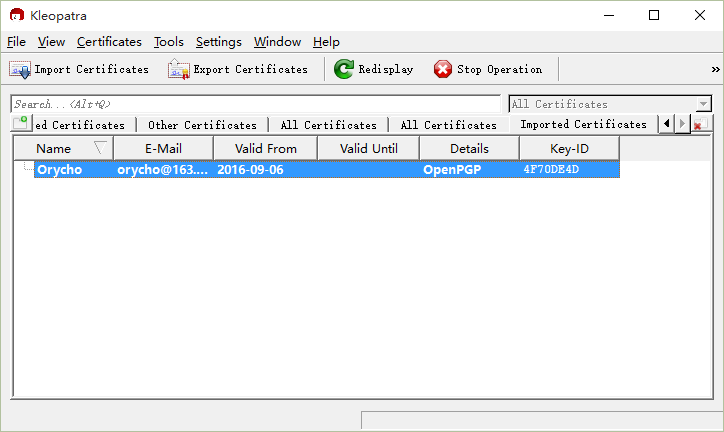
Then, we can get a certificate,
Certificate Export and Revocation
Exporting certificates is straightforward; right-click on the generated certificate and select “Export Certificates…” to export the public key certificate,
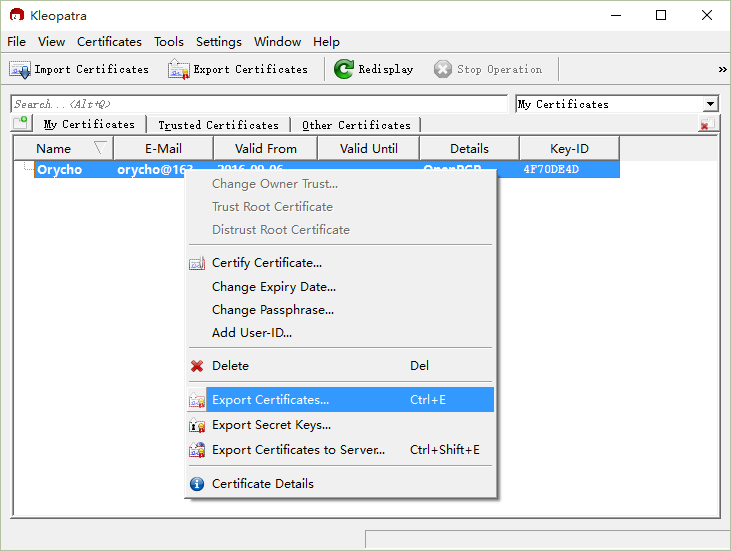
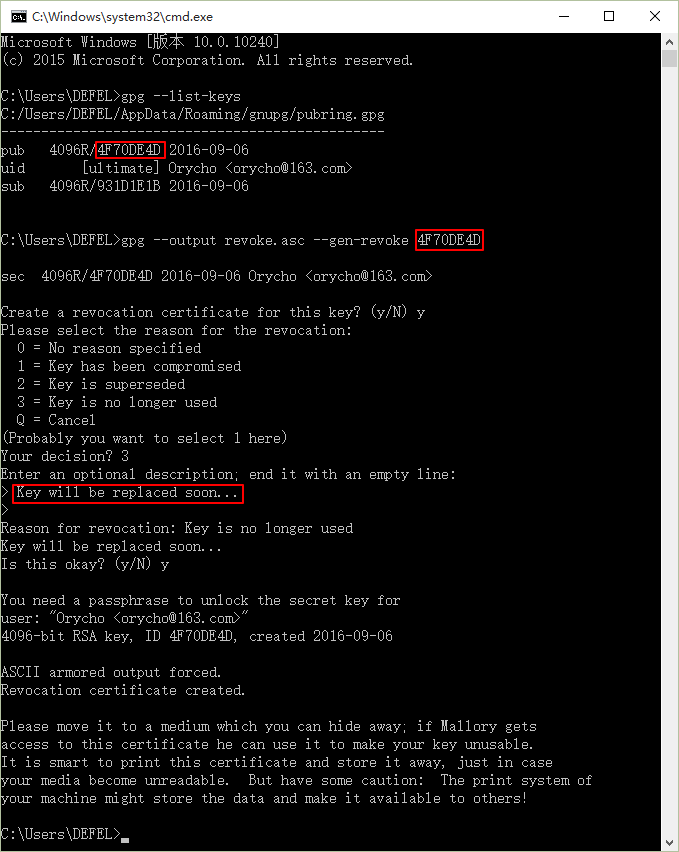
To deploy the public key certificate on a server, select “Export Certificates to Server…”. However, if it’s not our server, we cannot delete it once deployed, which can lead to information leaks if the key is compromised. Thus, creating a revocation certificate is necessary. This can only be done via the CMD command line,
1 | |
After identifying the certificate ID from the list, generate the revocation certificate with the specified command,
1 | |
Choose the reason for revocation,
- 0 = No reason specified
- 1 = Key has been compromised
- 2 = Key is superseded
- 3 = Key is no longer used
- Q = Cancel
Add some description, and finalize with the password. The revocation certificate will be located in the personal directory: %userprofile%,
Encrypting Data
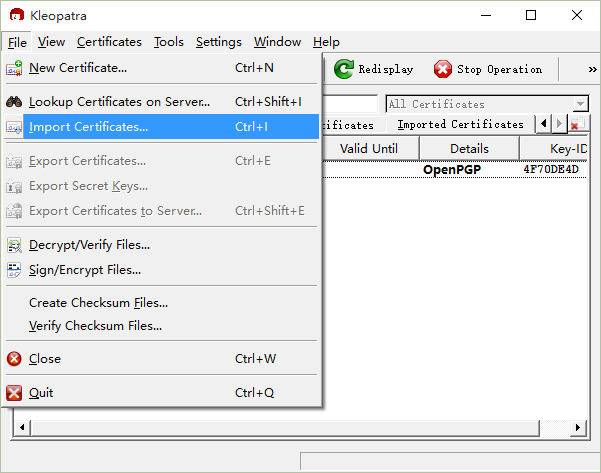
Encrypting information is relatively simple. If we don’t have the encryption certificate, we first need to import the public key certificate,
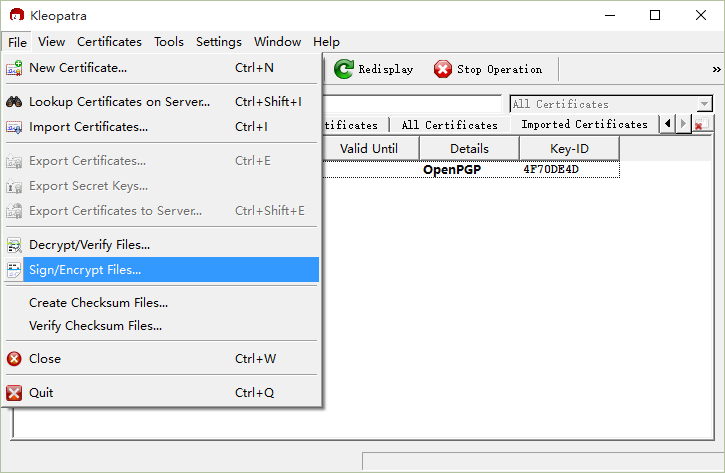
Select the “Encrypt/Sign” option from the menu,
Choose the file to encrypt or sign,
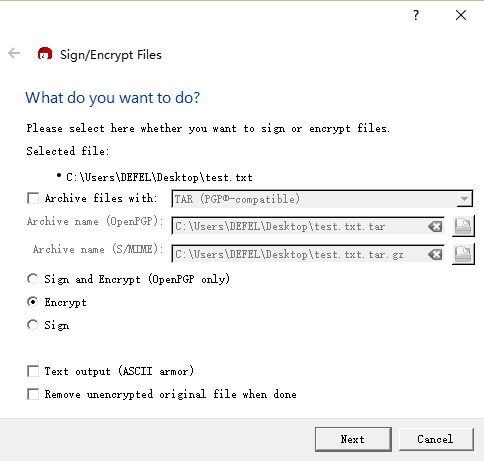
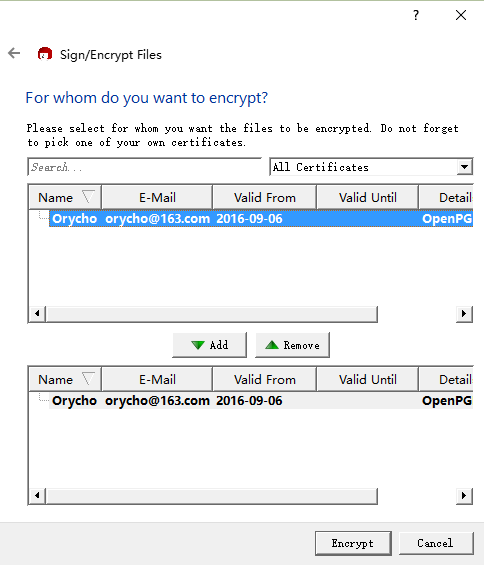
Then proceed to select the encryption and the corresponding certificate to complete the encryption process,
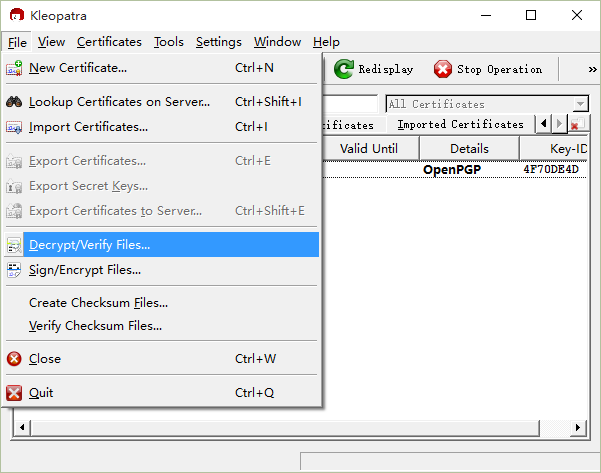
Decrypting Data
Decrypting an encrypted file follows similar steps to encryption. First, import the private key certificate, then proceed with the decryption process,
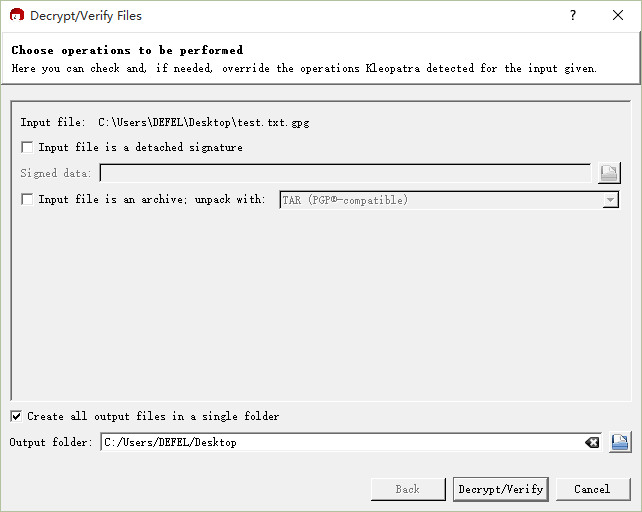
Choose the save location and whether the file has a signature,
Enter the private key certificate password,
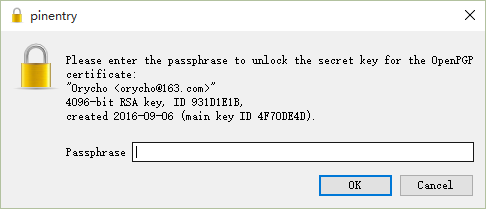
Decrypt successfully,
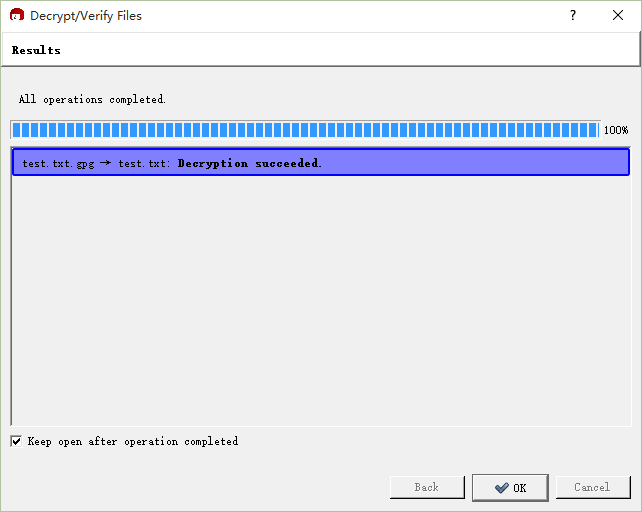
Additionally, files can be encrypted directly by right-clicking and selecting the encryption option from the menu.
Summary
Recently, I learned that enterprise QQ can monitor all client operations, similar to some corporate software and malware, which can directly monitor keyboard actions. While I wanted to implement this operation with Mathematica, the issues with binary file reading and control still persist, so it is more reliable to use the most common software for encryption.
PS: GPG4WIN can also be used to encrypt emails, here the LINK for more details.