 In the process of analyzing structures with OpenSees, the recorder command is essential. It records the displacements of critical nodes and elements in the structure, as well as the base reactions. Then we can use the data to plot the hysteresis curves of the structure. However, when OpenSees is adding data to a file using the recorder command, the file is locked, and it is not possible to access the recorded displacements in real-time during the model computation. To address this, the recorder provides an alternative method – sending data via TCP. By checking the recorder command,
In the process of analyzing structures with OpenSees, the recorder command is essential. It records the displacements of critical nodes and elements in the structure, as well as the base reactions. Then we can use the data to plot the hysteresis curves of the structure. However, when OpenSees is adding data to a file using the recorder command, the file is locked, and it is not possible to access the recorded displacements in real-time during the model computation. To address this, the recorder provides an alternative method – sending data via TCP. By checking the recorder command,
1 | |
There exists an option for -tcp, which according to the documentation,
1 | |
It requires an IP address and a port number. We can use Python to listen on a TCP port and thus acquire the analysis data. By using Python socket module to listen on a port, I’ve chosen port 8099 since it is less commonly used by other applications,
1 | |
First, I receive 20 bytes of data to see its content. Before listening, it is necessary to insert the following recorder code into the OpenSees script for the time-history analysis,
1 | |
Here, I record the displacements of three degrees of freedom for node 504 in the model. The node number is defined based on individual needs.
Running the Python code to listen data via TCP and the TCL code for time-history analysis directly, we can get the printed data: b’\x00\x00\x00\x00\x00\x00\x10@’. It is important to note that OpenSees sends data as a byte stream, so we need to decode the received data. In Python, byte streams can be decoded using the str.decode() method, but a more convenient method involves the Struct module:
This module performs conversions between Python values and C structs represented as Python bytes objects. This can be used in handling binary data stored in files or from network connections, among other sources. It uses Format Strings as compact descriptions of the layout of the C structs and the intended conversion to/from Python values.
Simply import struct module and use the unpack() function for decoding,
1 | |
When we construct a Struct object, we should use the structured code ‘d’ to denote the data as a 64-bit floating point. Struct supports many types of byte stream decoding,
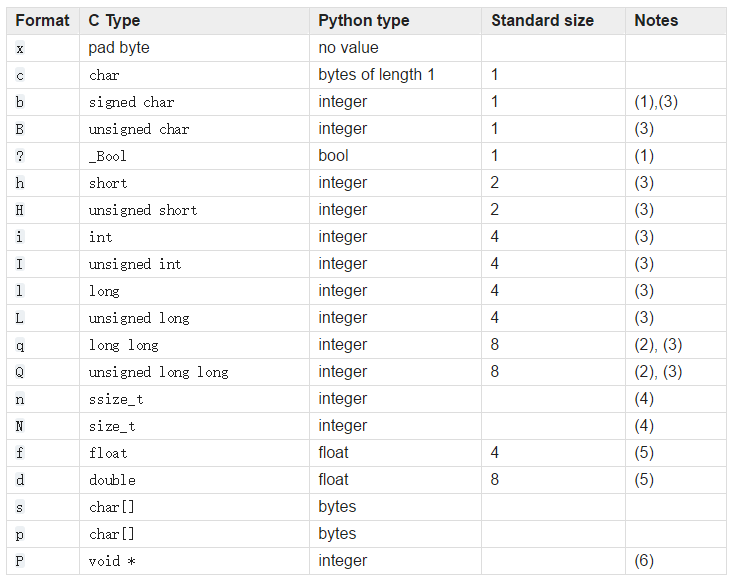
The Selection can be based on actual transmission requirement. Thus, we get the first piece of data: (4.0,), which actually indicates the size of the subsequent data. For a clearer understanding of the data transmission method, a loop can be used to fetch the data,
1 | |
We can get the following data,
1 | |
Clearly, the selected output information includes the current time and note displacements for the three degrees of freedom. Thus, the data can be interpreted as follows: the first segment of data represents the length of the data, and from the second segment, the data length, time, and displacements in the three degrees of freedom are sequentially output. Based on this rule, a simple loop is used to store all the data,
1 | |
Thus, we can get the following data now,
1 | |
This method successfully retrieves the TCP data transmitted by the recorder. Since TCP communication is more direct than file-based data retrieval and better suited for remote operations and distributed computing, this approach is more efficient from my perspective. Following this logic, a loop to listen on port 8099 can be created. The code below, modified from one found on the OpenSees forum, continually fetches data. We can use Python to start a subprocess to listen on port 8099 continuously. Once data is received, the main thread can proceed with subsequent tasks,
1 | |
It should be noted that this code works well in local testing, but during online testing, when the number of recorded nodes is large (hundreds of degrees of freedom), packet loss can occur. This can lead to decoding errors with Struct, resulting in abnormally large or small data, such as 5.8e+312 or 1.4e-217. Therefore, when using TCP to transmit data between multiple computers, we should write a Python script on the machine with OpenSees installed to receive data locally and transmit it to another machine using an appropriate data flow, this can ensures a reliable transmission.
All source code is available upon request.